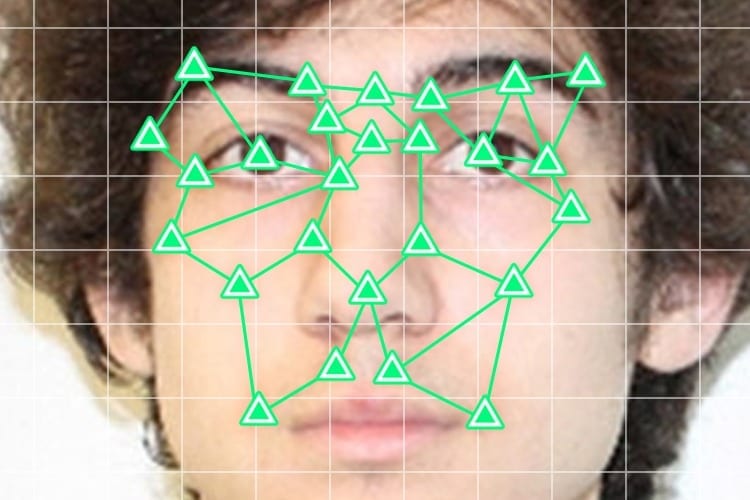
Facial recognition software, which American military and intelligence agencies used for years in Iraq and Afghanistan to identify potential terrorists, is being eagerly adopted by dozens of... Read more
Perpetrators can suppress “crime memories,” study finds It sounds just like something out of a sci-fi police procedural show—and not necessarily a good one. In a darkened room, a scientist i... Read more
Kidnappers used to make ransom notes with letters cut out of magazines. Now, notes simply pop up on your computer screen, except the hostage is your PC. In the past year, hundreds of thousan... Read more